Merkle proof: Simple guide to data verification in blockchain
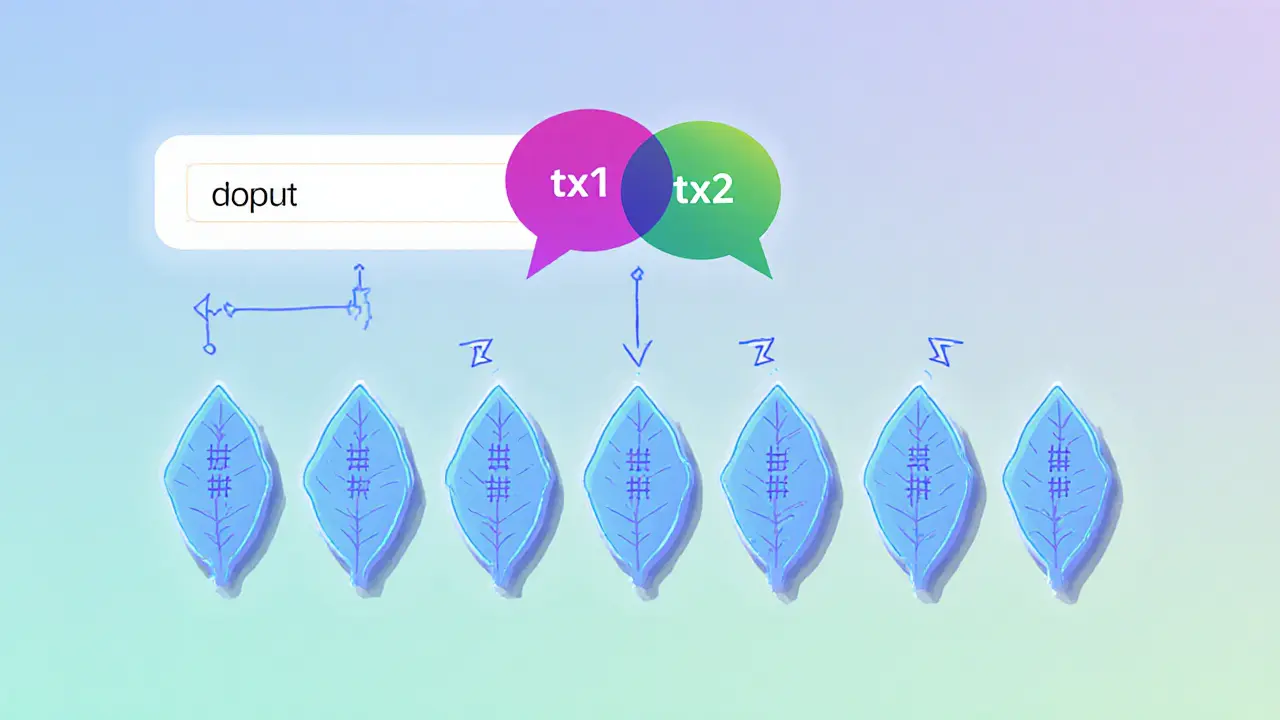
When working with Merkle proof, a cryptographic method that shows a piece of data belongs to a larger set without revealing the whole set. Also known as proof of inclusion, it lives inside a Merkle tree, a binary hash structure where each leaf holds a data hash and each parent node stores the hash of its children. The tree relies on cryptographic hash, a one‑way function that turns any input into a fixed‑size string, making tampering practically impossible. In short, a Merkle proof links a single leaf to the tree root, proving that the leaf is part of the set.
Why Merkle proofs matter for blockchain and beyond
Blockchains use Merkle proofs to confirm that a transaction sits inside a block without downloading the whole block. That means light wallets can verify balances quickly, saving bandwidth and storage. The proof also enables efficient cross‑chain communication: a smart contract on one chain can trust data from another by checking its Merkle root. Beyond crypto, Merkle proofs power data integrity checks in distributed file systems, audit logs, and even supply‑chain tracking, where you need proof that an item was recorded at a certain step without exposing the entire record.
In practice, generating a Merkle proof involves hashing the target data, then recursively hashing sibling nodes up to the root. The resulting list of sibling hashes is the proof you share. Anyone with the root hash can recompute the path and confirm inclusion. This simple yet powerful technique underpins many DeFi protocols, NFT marketplaces, and off‑chain scaling solutions like rollups. Below you’ll find a curated set of articles that dive deeper into real‑world uses, from exchange security reviews to tax implications of crypto transactions, all of which touch on how Merkle proofs keep the system trustworthy. Explore the collection to see how these concepts apply to regulations, airdrops, and the latest blockchain tools.
Learn how Merkle trees work in blockchain, why they boost security and efficiency, and get practical tips for building and verifying Merkle proofs.
Categories
Archives
Recent-posts
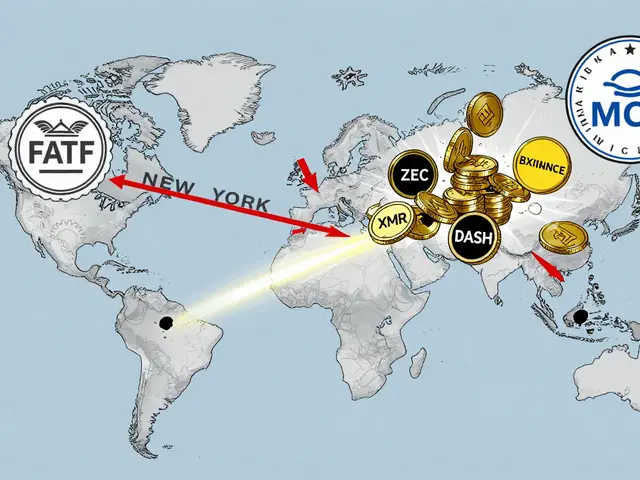
Privacy Coin Delisting Wave from Crypto Exchanges: Why Major Platforms Are Dropping XMR, ZEC, and DASH
Dec, 4 2025


 Finance
Finance