Merkle Tree Builder
Merkle Root:
When you hear Merkle trees are a type of cryptographic data structure that lets a blockchain prove that a transaction is in a block without needing to download the whole block. Each leaf node holds the hash of a single transaction, inner nodes hold the combined hash of their children, and the single top node - the Merkle root - acts as a digital fingerprint for the entire set of transactions.
Key Takeaways
- Merkle trees turn thousands of transactions into one short hash called the Merkle root.
- They enable lightweight verification called a Merkle proof, which only requires a few hashes.
- Bitcoin and Ethereum both use Merkle‑based structures, but the exact variant differs.
- Benefits include storage savings, fast verification, and tamper‑evidence.
- Limitations involve tree rebuilding for new data and difficulty proving non‑inclusion.
What Is a Merkle Tree?
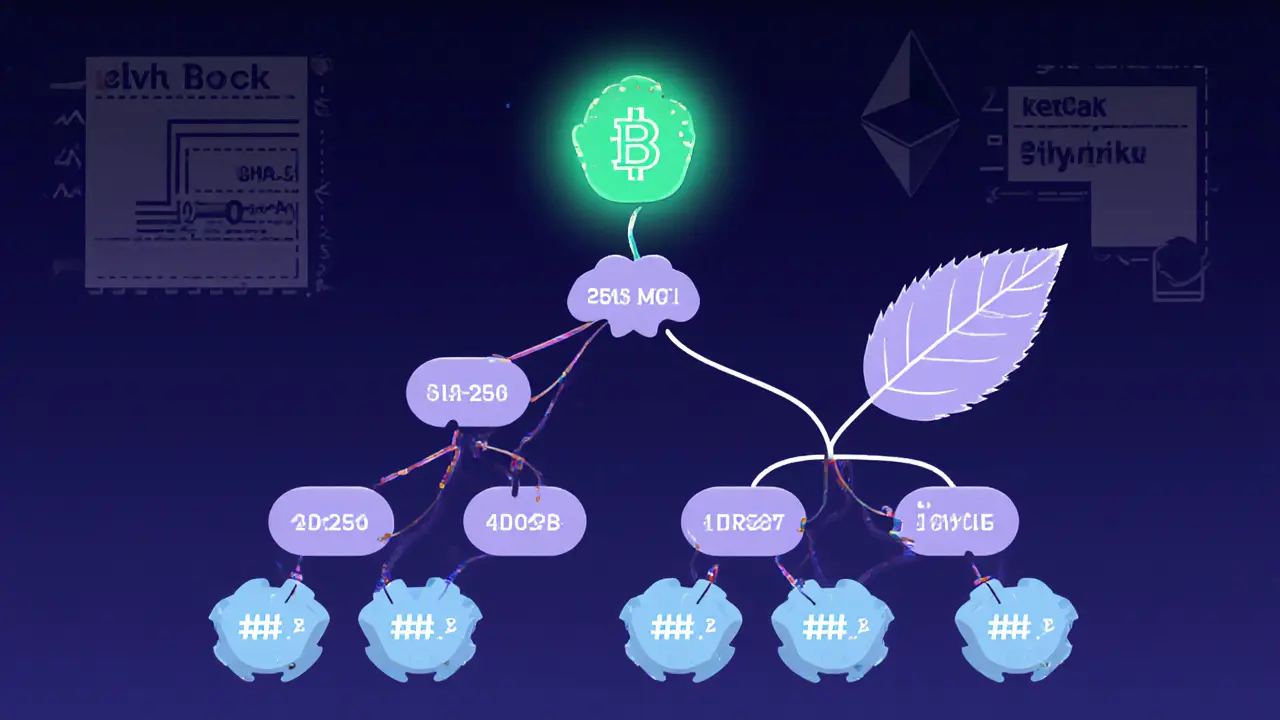
A Merkle tree - also known as a hash tree or binary hash tree - is a binary data structure where every node stores a cryptographic hash. The lowest level, called leaf node contains the hash of an individual transaction or piece of data. Moving up, each parent node concatenates the hashes of its two children and hashes the result again. This process repeats until it reaches the single top node, the Merkle root a hash that uniquely represents the entire set of leaf values.
The tree’s binary nature means it always has an even number of leaves. When a block has an odd number of transactions, the last hash is duplicated so the tree stays balanced. This rule keeps the algorithm simple and deterministic.
How Merkle Trees Power Blockchain
In a blockchain each block a collection of transactions packaged together contains a header and a body. The header stores the Merkle root, while the body holds the raw transactions. When a node receives a new block, it hashes every transaction, builds the Merkle tree, and compares the calculated root with the one in the header. If they match, the block is valid.
Bitcoin uses the SHA‑256 hash function for every step of this process. After hashing each transaction, the network repeatedly applies SHA‑256 to the concatenated child hashes until the Merkle root is produced. The root is then written into the block header, which is also part of the proof‑of‑work algorithm.
Ethereum takes a slightly different route. It employs a Merkle Patricia tree a hybrid structure that combines a Merkle tree with a Patricia trie for efficient key‑value storage. This variant lets Ethereum store account balances, contract code, and storage slots in a single cryptographic proof, making state validation fast for light clients.
Why Use Merkle Trees?
There are three big advantages:
- Storage efficiency: Instead of keeping every transaction on‑chain, a node can store just the Merkle root and still verify the entire block.
- Fast verification: A Merkle proof requires only log₂(N) hashes, where N is the number of transactions. For a block with 2,000 transactions, a proof needs only about 11 hashes.
- Tamper evidence: Changing a single transaction alters its leaf hash, which propagates up the tree and changes the Merkle root. Any mismatch instantly signals corruption.
Lightweight wallets and SPV (Simplified Payment Verification) clients rely on these proofs to confirm that a payment was included without downloading the whole blockchain.
Limitations and Challenges
Merkle trees are not a silver bullet. Adding a new transaction means rebuilding the tree, which can be costly for high‑throughput systems. Also, the structure proves inclusion but does not easily prove that a transaction is absent. Developers must handle edge cases like odd leaf counts and duplicate hashes.
From a developer’s perspective, implementing a Merkle tree involves understanding cryptographic hashing, tree traversal, and proof verification. A basic implementation can be written in a week, but optimizing for millions of transactions per day often takes months of profiling and tweaking.
Variants and Emerging Trends
Beyond the classic binary version, several specialized trees are gaining traction:
- Merkle Patricia tree used by Ethereum for state storage - combines Merkle proofs with a prefix tree to handle sparse key spaces.
- Sparse Merkle tree a depth‑fixed tree that can represent billions of possible keys with only a few stored leaves - popular in privacy‑preserving protocols.
- Quantum‑resistant hash functions are being explored to future‑proof Merkle proofs against potential quantum attacks.
- Layer‑2 solutions such as rollups often bundle many transactions into a single Merkle root, then post a succinct proof to the main chain.
Practical Tips for Building Your Own Merkle Tree
If you need to add Merkle support to a project, follow these steps:
- Choose a hash algorithm (SHA‑256 is standard for Bitcoin, Keccak‑256 for Ethereum).
- Collect all transaction data and compute the leaf hashes.
- If the leaf count is odd, duplicate the last hash.
- Iteratively pair hashes, concatenate them, and hash the result until you reach a single hash - the Merkle root.
- Store the root in your block header and expose a function that returns the proof (list of sibling hashes) for a given transaction index.
Common pitfalls:
- Mixing byte order when concatenating hashes - always use big‑endian consistent with the target blockchain.
- Forgetting to duplicate the last leaf on odd‑sized trees - this creates mismatched roots.
- Not handling the case where a proof is requested for an index out of range - return a clear error.
Many open‑source libraries already implement these steps. The Bitcoin Core repository, for example, provides a well‑tested C++ class, while JavaScript developers can use the "merkletreejs" package.
Merkle Tree vs. Simple Transaction List
| Aspect | Simple Transaction List | Merkle Tree |
|---|---|---|
| On‑chain size | All transactions stored in the block body | Only the Merkle root stored in the header |
| Verification data needed | Full block download | Logarithmic number of hashes (Merkle proof) |
| Proof of inclusion | Not available without full block | Instant via Merkle proof |
| Impact of a single transaction change | Only that transaction is altered | Entire Merkle root changes, signaling tampering |
| Complexity to implement | Very low | Moderate - requires hashing and tree logic |

Frequently Asked Questions
Frequently Asked Questions
What exactly does a Merkle proof prove?
A Merkle proof shows that a specific transaction’s hash appears in a block’s Merkle tree by providing the sibling hashes needed to reconstruct the Merkle root. If the reconstructed root matches the one in the block header, the transaction is confirmed as part of the block.
Why does Bitcoin duplicate the last hash when there’s an odd number of transactions?
Duplicating the last leaf keeps the tree perfectly balanced, which simplifies the hashing algorithm. Without duplication, some branches would be deeper than others, breaking the deterministic nature of the Merkle root.
Can a Merkle tree prove that a transaction is NOT in a block?
Standard Merkle trees are designed for inclusion proofs, not exclusion. To prove non‑inclusion you need a different structure, such as a sparse Merkle tree or a Merkle‑Patricia proof that can show an empty slot at a given index.
Is the Merkle root always stored in a block header?
Yes. In both Bitcoin and Ethereum the Merkle root (or its variant) is part of the block header, making it quick for nodes to verify the integrity of the whole transaction set without opening the full block.
How do Layer‑2 rollups use Merkle trees?
Rollups batch many transactions off‑chain, compute a Merkle root for the batch, and then post that single root to the main chain. A concise proof lets anyone verify any individual transaction inside the batch without pulling the whole rollup data.


 Finance
Finance



Matt Nguyen
November 11, 2024 AT 06:53While the casual reader might presume that Merkle trees are mere buzzwords, the underlying cryptographic rigor demands an appreciation seldom found in mainstream discourse. The subtlety lies in the deterministic duplication of odd leaves, which, if misapplied, can compromise the entire proof structure.
Katherine Sparks
November 13, 2024 AT 14:27Thank you for breaking down the concept so clearly; this explanation will certainly help newcomers navigate the complexities of blockchain verification. 🌟
Kimberly Kempken
November 15, 2024 AT 22:00Anyone who thinks Merkle trees are the holy grail of scalability is clearly overlooking the inherent latency introduced by repeated hashing; the supposed efficiency is a myth propagated by overhyped whitepapers.
Kortney Williams
November 18, 2024 AT 05:33While the performance concerns are valid, it’s worth noting that many implementations mitigate latency through parallel processing, preserving the benefits of logarithmic proof sizes.
Laurie Kathiari
November 20, 2024 AT 13:07It is a disgrace that developers ignore the ethical implications of opaque data structures; transparency demands that every participant understand how a Merkle root encapsulates collective trust.
Promise Usoh
November 22, 2024 AT 20:40Indeed, the philosophical underpinnings of trust in distributed ledgers rest upon the immutable nature of the root; any deviation erodes the social contract inherent in blockchain ecosystems.
Amal Al.
November 25, 2024 AT 04:13Merkle trees, by design, compress thousands of transaction hashes into a single fingerprint; this not only saves storage but also enables rapid validation-crucial for lightweight clients!!!
Natalie Rawley
November 27, 2024 AT 11:47Oh, the drama of a single hash whispering the fate of an entire block-it's as theatrical as any Shakespearean tragedy!
Scott McReynolds
November 29, 2024 AT 19:20In the grand tapestry of blockchain architecture, Merkle trees occupy a central, almost mythic, position.
Their elegance stems from a simple premise: recursively hash pairs of data until a singular root emerges.
This root, immutable by design, acts as a cryptographic seal that binds every leaf beneath it.
When a node wishes to verify a transaction, it need not download the entire block; instead it requests a Merkle proof consisting of sibling hashes.
The proof, typically logarithmic in size relative to the number of transactions, allows the verifier to reconstruct the root and compare it against the header.
The beauty of this approach lies in its scalability: even as transaction volumes soar into the millions, the proof size grows only linearly with the depth of the tree.
Moreover, the deterministic duplication of the last leaf in odd-sized trees guarantees a balanced structure, eliminating edge‑case inconsistencies.
From a security perspective, any alteration to a single leaf ripples upward, mutating the root and instantly flagging tampering.
This property underpins the trustlessness of decentralized networks, where participants can independently validate data without relying on a central authority.
Implementations differ, however; Bitcoin adheres to a pure binary Merkle tree using SHA‑256, while Ethereum adopts a Merkle‑Patricia trie to accommodate sparse key‑value mappings.
The latter trades simplicity for flexibility, enabling efficient state proofs that encompass account balances and contract storage.
In practice, developers often leverage existing libraries-such as Bitcoin Core’s C++ classes or JavaScript’s merkletreejs-to avoid reinventing wheel.
Nevertheless, performance tuning remains non‑trivial, especially when aiming for sub‑second proof generation at high throughput.
Profiling tools can expose bottlenecks in hash computation, prompting optimizations like SIMD‑accelerated SHA‑256.
Ultimately, the decision to employ a Merkle structure should be guided by the specific requirements of the application, balancing proof size, verification speed, and implementation complexity.
In summary, Merkle trees provide a robust framework for efficient, tamper‑evident verification, cementing their role as a foundational pillar of modern blockchain systems.
Alex Gatti
December 2, 2024 AT 02:53Indeed, the logarithmic proof size is the key performance win.
John Corey Turner
December 4, 2024 AT 10:27Consider the Merkle root as the soul of a block-an indivisible essence that reflects the collective history of its constituents.
Jenise Williams-Green
December 6, 2024 AT 18:00To treat that soul as a mere data point is to betray the very principle of integrity that blockchain purports to uphold.
Adarsh Menon
December 9, 2024 AT 01:33Oh sure, because duplicating a hash for an odd leaf is the pinnacle of innovation-how groundbreaking!
Jim Griffiths
December 11, 2024 AT 09:07Actually, the duplication ensures a complete binary tree, which simplifies the proof algorithm and maintains determinism.
Rob Watts
December 13, 2024 AT 16:40Merkle proofs keep wallets lightweight.
Bhagwat Sen
December 16, 2024 AT 00:13You might think it's simple, but neglecting the proof construction details can expose clients to subtle security flaws.
Cathy Ruff
December 18, 2024 AT 07:47Anyone still using naive implementations clearly hasn't read the latest security audits; they’re inviting attacks.
Amy Harrison
December 20, 2024 AT 15:20Let's keep the community informed and safe! 🚀
mukesh chy
December 22, 2024 AT 22:53Because what the world really needed was another layer of complexity masquerading as a solution.
Marc Addington
December 25, 2024 AT 06:27Patriotically, we must reject foreign-designed cryptographic fluff and stick to proven, homegrown hash structures.