Imagine sending your medical records to a cloud server so a doctor can analyze them - but the server never sees your actual data. Not your name, not your diagnosis, not even your age. Just encrypted numbers. And yet, the server still gives you a correct result: "Your risk for diabetes is 12%." That’s not science fiction. It’s homomorphic encryption.
This isn’t just another encryption method. Traditional encryption protects your data when it’s stored (at rest) or being sent (in transit). But what about when it’s being used? That’s the blind spot. Homomorphic encryption closes it. It lets computers work on encrypted data without ever decrypting it. The result? Privacy you can’t break - even if the system itself is hacked.
How Homomorphic Encryption Actually Works
At its core, homomorphic encryption is about preserving math. Normally, if you encrypt the number 5 and the number 3, you get two random-looking strings. You can’t add them. But homomorphic encryption makes sure that if you add the encrypted versions, you get an encrypted result that, when decrypted, equals 8.
It works because the encryption algorithm is designed to keep mathematical relationships intact. Addition and multiplication on ciphertexts produce ciphertexts that correspond to the same operations on the original numbers. Think of it like doing arithmetic with gloves on. You can’t feel the object, but you can still move it around, twist it, stack it - and someone with the right key can see the final shape.
This isn’t magic. It’s built on advanced math - number theory, lattice problems, modular arithmetic. But you don’t need to understand the math to use it. You just need to know that if you encrypt your data with a homomorphic scheme, you can send it to a third party, ask them to run calculations, and get back a correct answer - without ever giving up control of your data.
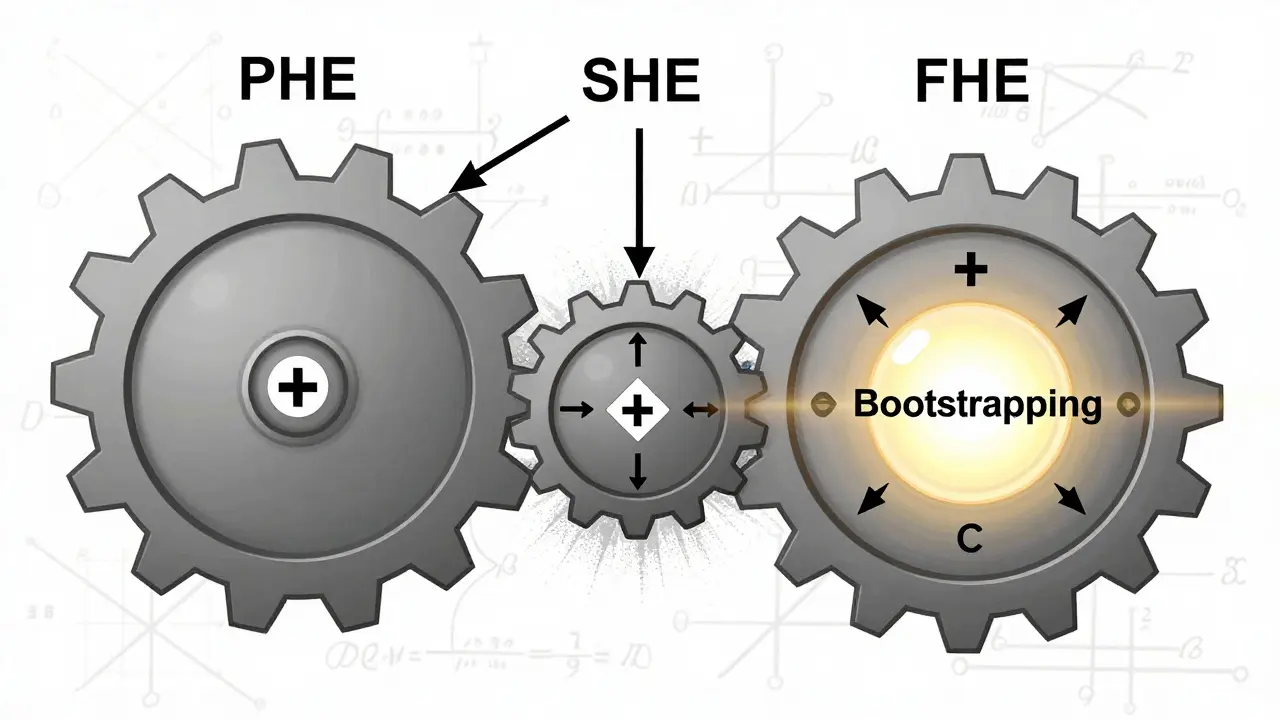
The Three Types: PHE, SHE, and FHE
Not all homomorphic encryption is the same. There are three main types, each with different power and limits.
- Partially Homomorphic Encryption (PHE) lets you do one operation - either addition or multiplication - over and over. RSA encryption is an example. It’s useful for simple tasks like tallying encrypted votes or payments, but not much else.
- Somewhat Homomorphic Encryption (SHE) allows both addition and multiplication, but only a limited number of times. After too many operations, the encrypted data gets too "noisy" and becomes unreadable. It’s like a battery that runs out after a few calculations.
- Fully Homomorphic Encryption (FHE) is the holy grail. It supports unlimited additions and multiplications. No matter how complex the calculation - a logistic regression, a neural network, a financial model - FHE can handle it. The breakthrough came in 2009 from Craig Gentry, who built the first working FHE system using a technique called "bootstrapping" to clean up noise and keep the encryption alive.
FHE is what people mean today when they talk about homomorphic encryption. It’s the only version that can truly unlock the potential of privacy-preserving computation.
Why This Matters for Privacy
Most data breaches happen because systems need to decrypt data to process it. Hospitals store patient records in plain text so AI models can predict disease risks. Banks decrypt transaction histories to detect fraud. That’s a huge risk. If an attacker gets in, they get everything.
Homomorphic encryption flips that. Data stays encrypted from start to finish. A cloud provider can run machine learning models on encrypted health records and return accurate predictions. A bank can check if a loan applicant qualifies - without ever seeing their income, credit score, or spending habits.
This isn’t theoretical. In 2022, a consortium of European hospitals used FHE to analyze 10,000 genomic datasets. No raw DNA data left the patients’ devices. The cloud server never saw a single base pair. Yet, they still found genetic links to rare diseases. That’s the power: analysis without exposure.
Regulators are taking notice. GDPR, HIPAA, and CCPA all require "privacy by design." Homomorphic encryption is one of the few technologies that actually meets that standard.
Real-World Use Cases Today
While FHE is still emerging, it’s already being used in high-stakes environments:
- Healthcare: Analyzing patient data across hospitals without sharing records. Predicting outbreaks, identifying drug interactions, and matching donors for organ transplants - all encrypted.
- Finance: Credit scoring without access to income statements. Fraud detection without seeing transaction details. Private risk modeling for insurance underwriting.
- Government: Secure voting systems where ballots are counted without revealing who voted for whom. Tax audits where citizens submit encrypted income data.
- AI Training: Training machine learning models on encrypted data. A company can use customer data to improve its product - without ever storing that data in plain text.
One financial services firm in the U.S. spent eight months and over $500,000 to deploy FHE for encrypted credit scoring. The result? A 40% reduction in fraud detection false positives - and zero exposure of customer data.
The Big Catch: Performance and Complexity
Homomorphic encryption isn’t magic. It’s slow. And heavy.
Encrypting a single number can turn a 4-byte integer into 1.5 megabytes of ciphertext. Running a simple addition might take 100 milliseconds instead of 0.0001 milliseconds. Multiply that by thousands of operations in a machine learning model, and you’re looking at hours of compute time.
Hardware helps. Modern CPUs with AVX2 or AVX-512 instructions can speed things up. But even then, FHE is 10,000 to 1,000,000 times slower than plain computation. Memory demands are brutal too - 16GB of RAM is the bare minimum for anything beyond tiny tests.
And then there’s the learning curve. Developers need to understand lattice-based cryptography, noise management, and circuit optimization. One Reddit user spent two weeks just tuning parameters for a logistic regression model. "FHE is unforgiving," they wrote. "One wrong bit, and the whole thing breaks."
Libraries like Microsoft SEAL, IBM’s HElib, and OpenFHE help - but they’re still for cryptographers, not app developers. Zama’s Concrete ML is trying to change that, letting data scientists train models on encrypted data with Python - but it’s still early days.

What’s Changing Fast
The pace of improvement is accelerating. In 2023, the Open Source Privacy Engineering group released the first FHE interoperability standards. That means code written for one library can now work with another. No more vendor lock-in.
Hardware is catching up too. Intel’s SGX and AWS’s Nitro Enclaves now support FHE acceleration. Google’s research team showed how to optimize FHE for neural networks - cutting training time by 70%.
Algorithmic breakthroughs are happening. Researchers are building "leveled" FHE schemes that reduce bootstrapping - the biggest performance killer. One 2023 study showed a 12x speedup by eliminating unnecessary noise refresh cycles.
Market analysts expect the FHE market to grow from $120 million in 2023 to $1.2 billion by 2027. Gartner says it’s past the hype phase - now it’s in the "early adopter" stage. Banks, insurers, and healthcare providers are testing it. Not because it’s easy. But because the alternative - data breaches, regulatory fines, lost trust - is worse.
Is It Ready for You?
If you’re a developer building a consumer app? Probably not yet. The overhead is too high. The tools are too complex.
If you’re in a regulated industry handling sensitive data? Then you should be testing it - now.
Start small. Encrypt a single dataset. Run one simple calculation. See how it behaves. Measure the latency. Track the memory use. Talk to your cloud provider - Microsoft Azure, Google Cloud, and IBM Cloud all offer FHE-ready environments.
Homomorphic encryption won’t replace TLS or AES. But it will become the layer that protects data when it matters most - when it’s being used. And as regulations tighten and breaches grow more costly, that layer won’t be optional. It’ll be essential.
Can homomorphic encryption be hacked?
Homomorphic encryption itself is mathematically secure - breaking it would require solving problems that are believed to be impossible for classical computers, even with future quantum computers. But the system around it can be hacked. Poor key management, flawed implementations, or side-channel attacks (like timing or power analysis) can leak information. The encryption is strong, but the software using it isn’t always.
Is homomorphic encryption the same as zero-knowledge proofs?
No. Zero-knowledge proofs let one party prove they know something (like a password) without revealing it. Homomorphic encryption lets someone perform operations on encrypted data and return a result - without ever seeing the data. One is about proving knowledge; the other is about computing on secrecy.
What’s the difference between FHE and traditional encryption like AES?
AES encrypts data so it can’t be read or modified without the key. But to use it - to search, analyze, or calculate - you have to decrypt it first. FHE lets you compute on the encrypted data directly. AES protects data at rest and in transit. FHE protects data in use - the last missing piece.
Can I use homomorphic encryption on my phone or laptop today?
You can experiment with it - libraries like Microsoft SEAL have mobile demos. But performance is terrible on consumer hardware. A simple calculation might take 10 seconds. For real-world use, you need server-grade CPUs, lots of RAM, and optimized code. It’s not ready for consumer apps yet.
Will homomorphic encryption replace blockchain for privacy?
Not replace - complement. Blockchain ensures trust through decentralization and immutability. Homomorphic encryption ensures privacy during computation. They solve different problems. Some projects combine them: storing encrypted data on-chain and processing it off-chain with FHE. Together, they create systems that are both private and transparent.
What Comes Next
The future of homomorphic encryption isn’t about making it faster - it’s about making it easier. The goal is to hide the complexity. Imagine a cloud API where you upload encrypted data, call a function like "calculate_average," and get back an encrypted result. No cryptography knowledge needed.
That’s the vision. And it’s not far off. With hardware acceleration, standardized APIs, and open-source tools maturing, we’re moving from a niche for cryptographers to a foundational layer for secure computing.
By 2030, homomorphic encryption won’t be a buzzword. It’ll be in the background - like HTTPS. You won’t notice it. But you’ll depend on it.



 Finance
Finance