Hash Tree: The Backbone of Blockchain Security
When working with hash tree, a hierarchical structure of cryptographic hashes that lets you verify large data sets with a single digest. Also known as Merkle tree, it enables fast and secure proof of data inclusion without exposing the whole dataset, you instantly get a tool that’s essential for anyone dealing with distributed ledgers. In plain terms, a hash tree turns a massive list of records into a tiny fingerprint you can trust. That simple idea fuels everything from Bitcoin's block validation to modern DeFi airdrop proofs.
Why Cryptographic Hash Functions Matter
Any cryptographic hash function, a mathematical algorithm that converts any input into a fixed‑size string of characters is the engine behind a hash tree. Without a strong hash function, the tree’s security collapses. Functions like SHA‑256 produce outputs that are practically impossible to reverse or collide, meaning a single altered transaction instantly breaks the entire tree’s checksum. This property lets miners, auditors, and traders spot tampering in seconds, keeping the ledger honest.
In the world of crypto, the link between hash trees and blockchain, a distributed database that records transactions across many nodes is inseparable. Each block stores the root hash of its transaction list, so anyone can verify the whole block by checking one small value. If a single transaction is changed, the root hash changes, and the network rejects the block. This cascade effect is what makes double‑spending virtually impossible.
Beyond basic transaction validation, hash trees enable hash tree-based proofs that are lightweight enough for mobile wallets and IoT devices. Imagine a tiny sensor that needs to prove its data was recorded on a public ledger – it only needs to transmit a short Merkle proof instead of the full dataset. That efficiency is why many new projects, from decentralized storage to NFT marketplaces, embed Merkle proofs into their smart contracts.
Data integrity isn’t just a buzzword; it’s a concrete guarantee that the information you rely on hasn’t been altered. With a hash tree, you can verify the integrity of massive files – think of a gigabyte‑size software release – by downloading just the root hash and a few sibling nodes. This approach is now standard in blockchain‑based supply‑chain tracking, where each step of a product’s journey is logged and can be independently audited.
Smart contracts leverage hash trees to handle complex conditional logic without bloating the chain. For example, an airdrop program can distribute tokens to thousands of users by storing a Merkle root on‑chain and letting each recipient submit a proof of eligibility. This method saves gas, cuts transaction costs, and prevents spam attacks. The same technique powers many of the airdrop guides you’ll find on UpdatePool, like the Bull Finance or SupremeX token drops.
Decentralized applications (dApps) also use hash trees for off‑chain data fetching. A DeFi platform might store price feeds off‑chain but anchor a Merkle root on‑chain. When a user queries a price, the system provides a Merkle proof that the price came from the trusted feed. This hybrid model keeps the blockchain light while preserving trustlessness.
Looking ahead, new protocols are experimenting with recursive hash trees, where a tree’s leaves are themselves roots of other trees. This layering could enable ultra‑scalable roll‑up solutions and cross‑chain bridges, opening the door to truly global, interoperable ledgers. As the ecosystem evolves, understanding the basics of hash trees becomes a competitive edge for traders, developers, and investors alike.
Below you’ll find a hand‑picked selection of articles that dive deeper into how hash trees intersect with real‑world crypto topics. From regulatory updates that affect how airdrops are reported, to detailed exchange reviews that mention Merkle‑based security features, the collection gives you both the technical foundation and the market‑focused insights you need to stay ahead. Explore the posts to see hash trees in action across the crypto landscape.
Learn how Merkle trees work in blockchain, why they boost security and efficiency, and get practical tips for building and verifying Merkle proofs.


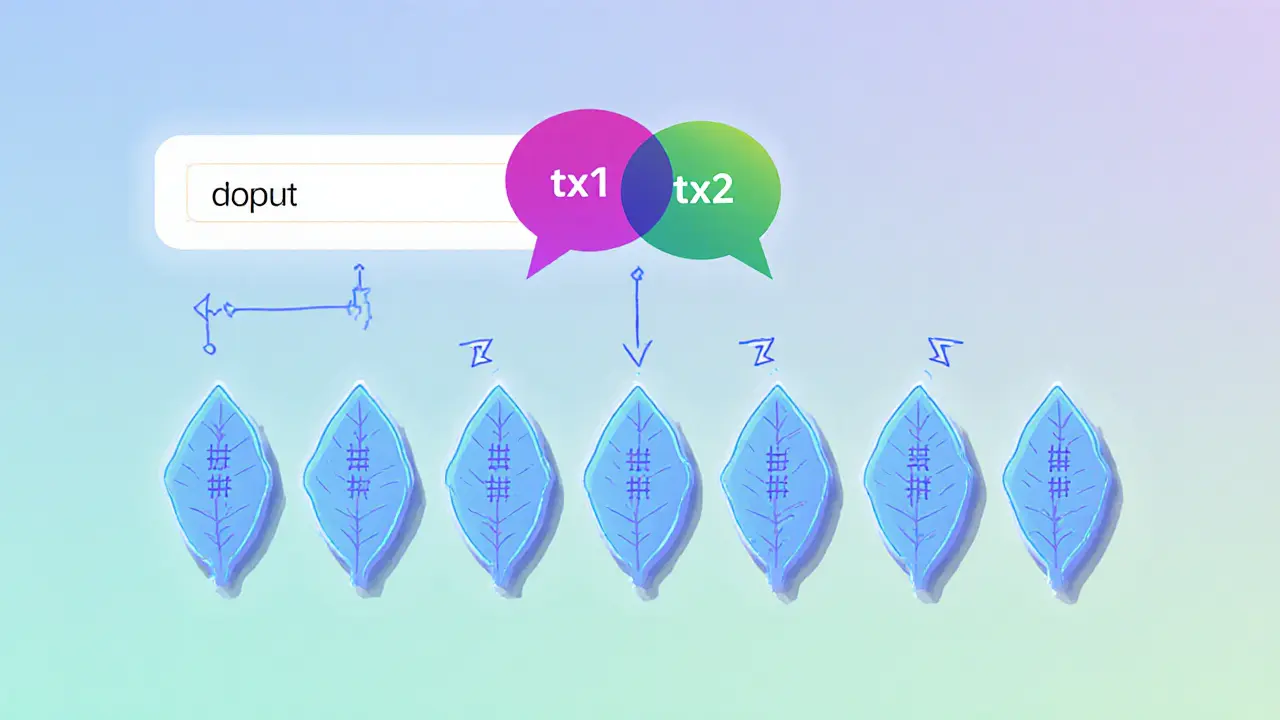
 Finance
Finance